
A takedown request said the GitHub account was “hosting and distributing leaks of internal code which poses significant risk to BINANCE.”


A takedown request said the GitHub account was “hosting and distributing leaks of internal code which poses significant risk to BINANCE.”

Comment
I hope nobody loses their shirt over this.
Summary
Mutter, Giuranna, Marriner - Mozart - Sinfonia concertante for Violin and Viola in E-Flat Major, K. 364: II. Andante (Academy of St Martin in the Fields)

Click to view this content.
Self help and cleaning advice
Some problems do seem to belong under the rug. Out of sight, out of mind.

Users of the Firefox browser for Android have been reporting that they are seeing a blank page when trying to load the main Google Search site.


The issue:
Android users with Firefox can't access Google Search (including intl sites and localized domains like google.de, .co.uk, .com.br). Instead, they see a blank page.
Cause:
A server-side bug on Google's end related to User-Agent (UA) sniffing, which serves an empty page to newer Firefox versions.
Affected versions:
All Firefox versions on Android (>= 65) including Mobile 121.0, Nightly 123, and older.
Chrome not affected:
The bug is specific to Firefox.
Solutions:
Advanced users can:
Status:
Additional notes:

Our behaviour and decisions can vary with the changing of the seasons. The trick is to learn to make the most of this natural variation.


Main findings:
Key takeaways:
which shall be now known as the pawtop.
Probably got some parachute built in.
That seems like a workout/endurance machine!
username checked out... 🤪

NIST raises an alarm on AI's privacy & security risks. Discover how AI systems like ChatGPT face new threats.


Key Points:
Smetana: Vltava (The Moldau) - Slovenian Youth Orchestra

Click to view this content.
Yeah, it's freakish because everything looks all wrong.
Of course if you care to look carefully, and sometimes closely.
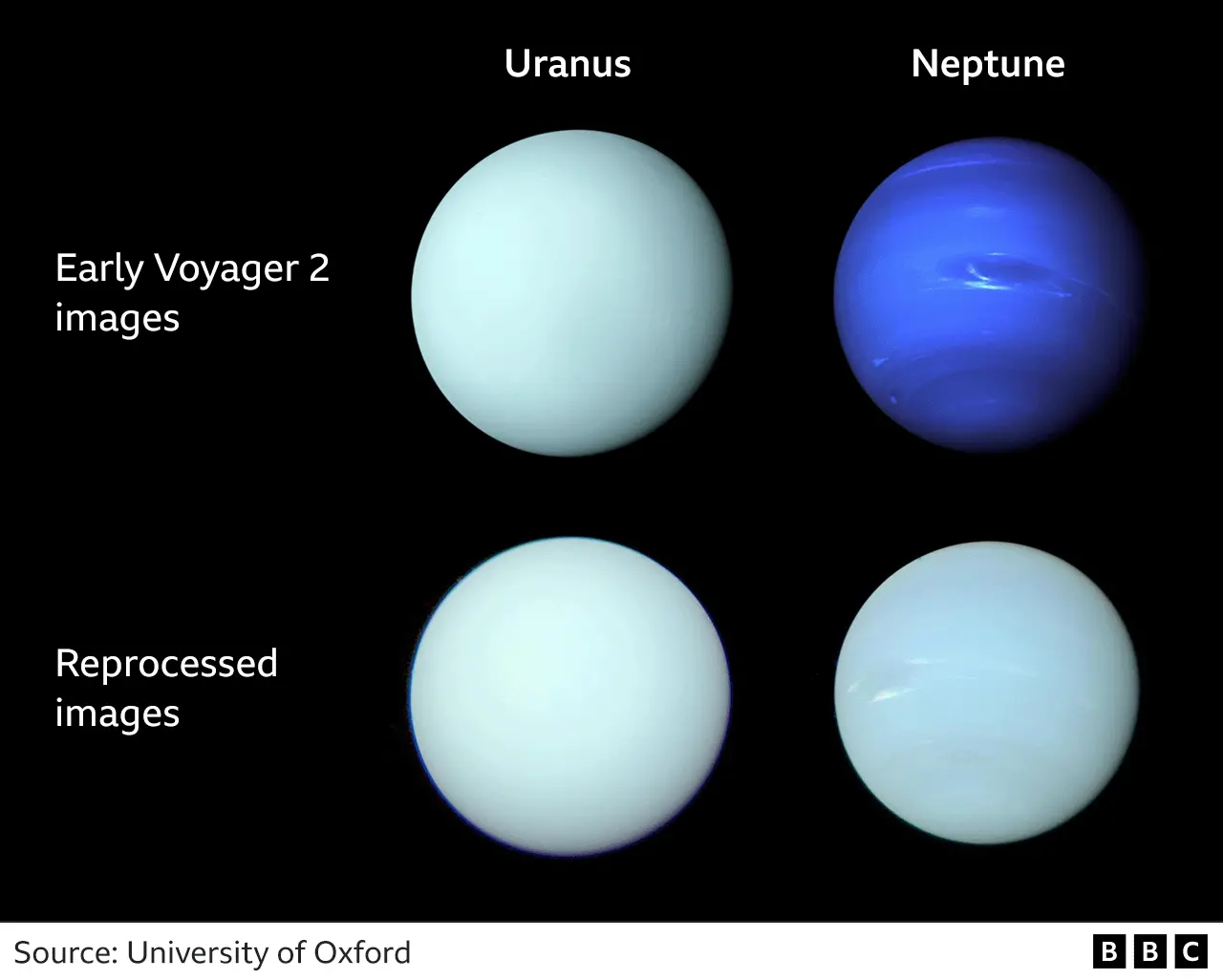
Uranus' color isn't green, it's greenish-blue, and so is Neptune's: Neptune and Uranus seen in true colours for first time

Analysis shows that our ideas of the colours of the planets Neptune and Uranus have been wrong.

Smiling ain't gonna save ya!
Deeply discounted, yet with the satisfying conclusion that our external clients get! /s
"Don't even think about petting me."
This Golden Retriever is Nursing 3 African Painted Dog Pups at Indiana Zoo After Mother Abandoned Them

Key points:
Additional details:

Global law firm Orrick, which works with companies affected by security incidents and hacks, has experienced its own data breach.

cross-posted from: https://zerobytes.monster/post/5063838
I guess if the law firm handles its own data breach this way; you can expect the companies to handle the breaches the same way.
Summary
The international law firm Orrick, Herrington & Sutcliffe, specializing in handling security incidents for companies, suffered a cyberattack in March 2023, resulting in the exposure of sensitive health information belonging to over 637,000 data breach victims.
The stolen data included consumer names, dates of birth, postal address and email addresses, and government-issued identification numbers, such as Social Security numbers, passport and driver license numbers, and tax identification numbers. The data also includes medical treatment and diagnosis information, insurance claims information — such as the date and costs of services — and healthcare insurance numbers and provider details.
Orrick, serving as legal counsel during security incidents at other companies, revealed that the b
And definitely not standing at the back end!
A paramour came to a shitty end...
There began a night, wet and dreary...
Cool computers!

You carry literal pieces of your mom—and maybe your grandma, and your siblings, and your aunts and uncles.

Summary:
The article discusses the phenomenon of microchimerism, where cells from a developing fetus can integrate into the mother's body and persist for years, potentially influencing various aspects of health. This bidirectional transfer of cells between mother and fetus during pregnancy is suggested to occur in various organs, such as the heart, lungs, breast, colon, kidney, liver, and brain. These cells, referred to as microchimeric cells, are genetically distinct entities that may play a role in immune system development, organ acceptance in transplantation, and even influencing behavior.
Researchers propose that microchimeric cells might impact susceptibility to diseases, pregnancy success, and overall health. Studies in mice suggest that these cells acquired during gestation could fine-tune the immune system and contribute to successful pregnancies. The article explores potential benefits and drawbacks of microchimerism, including its role in autoimmune diseases, organ acc

Your Android device has a powerful system for helping you recall almost anything imaginable, but — oh, yes — it's up to <em>you</em> to remember to use it.

Summary:
The author reflects on the challenges of memory and highlights a forgotten but valuable feature of Google Assistant on Android. The feature, called "Open memory," serves as a hub for Assistant's cross-platform information-storing system. Users can ask Google Assistant to remember specific information, and the "Open memory" command allows them to access a comprehensive list of everything stored, making it a useful tool for recalling details from any device connected to Google Assistant. The article emphasizes the potential of this feature for aiding memory and suggests incorporating it into daily habits for better recall.
You figure out where you want to go. Plan how to get there, and then do things in the present to get there. Don't get stressed out how things turn out; you can only really have some notion of control of what you are doing. If the current plan doesn't work, change it, and keep doing it, until you get there, or not.
2FAS, Bitwarden, Firefox are my most used FOSS on Android for me.
Grandma got to pet Penguin

Click to view this content.
Full Story
Summary
An elderly woman named Christine Cross has always been a huge fan of penguins. For Christmas, her daughter Lindsay fulfilled Christine's lifelong dream of petting a real penguin at SeaWorld San Diego. Christine was so overcome with emotion that she cried tears of joy.
Christine has always felt a connection to penguins because they are clumsy on land but graceful in the water, just like her. She collects anything penguin-themed and has sponsored penguins in zoos for years.
Lindsay said that when she told Christine about the present, "she didn't say any words. It was more like an excited noise." After the experience, Christine couldn't stop saying thank you.
Oh, the horror! I think I did the best I possibly could, given the circumstances.
Welcome, to the Twilight Zone...
Screwed!
But this is not a very good/logical/reasonable alien to be in contact with. There are so many ...ists with can call this alien. Generalization with sample of one? Pfff... They won't even get here...
It keeps getting bigger and better...
Pilipinas? This is definitely pornographic.
I guess people will cheat and hide it everywhere.

A new sextortion scam is making the rounds that pretends to be an email from the adult site YouPorn, warning that a sexually explicit video of you was uploaded to the site and suggesting you pay to have it taken down.

Summary
A new sextortion scam is circulating, impersonating YouPorn. Victims receive an email claiming that a sexually explicit video of them has been uploaded to the site and must pay to have it removed. In the past, similar scams threatened to share explicit content with contacts unless a ransom was paid, generating substantial profits. This recent scam claims to be from YouPorn, offering a free removal link that leads to nothing and lists paid options ranging from $199 to $1,399. Victims are urged to pay via Bitcoin. Thankfully, this campaign has not been successful, but it's important to remember that these emails are scams. If you receive such an email, delete it; there is no actual video, and making payments is not advisable.
Northwestern tower of the Forbidden City, Xicheng, Beijing, China by long10000



NightOwl was supposed to make Macs work in dark mode. After a recent update, one developer discovered it was siphoning users’ data through a botnet.

Short Summary
The macOS app called NightOwl, originally designed to provide a night mode feature for Macs, has turned into a malicious tool that collects users' data and operates as part of a botnet. Originally well-regarded for its utility, NightOwl was bought by another company, and a recent update introduced hidden functionalities that redirected users' data through a network of affected computers. Web developer Taylor Robinson discovered that the app was running a local HTTP proxy without users' knowledge or consent, collecting users' IP addresses and sending the data to third parties. The app's certificate has been revoked, and it is no longer accessible. The incident highlights the risks associated with third-party apps that may have malicious intentions after updates or ownership changes.
Longer Summary
The NightOwl app was developed by Keeping Tempo, an LLC that went inactive earlier this year. The app was recently found to have been turned into a botnet by the new o

Police raid on Marion County Record underscores digital security threats to media orgs.

Summary
Main Take-aways

Boffins build automated system to smash safety guardrails

Paper & Examples
"Universal and Transferable Adversarial Attacks on Aligned Language Models." (https://llm-attacks.org/)
Summary
MoustachedBouncer: Espionage against foreign diplomats in Belarus, probably collaborating with the Belarus government, by tricking Windows OS
A group titled MoustachedBouncer committing espionage against foreign embassies in Belarus has been identified by ESET Research.
News article: https://techcrunch.com/2023/08/10/belarus-hackers-target-foreign-diplomats/
News Summary
Facial recognition tech lands innocent woman with bogus carjacking charge

We take a look at another case of facial recognition technology getting it wrong in the land of law enforcement.

Summary